Table of contents
- What is Door Access Control?
- Types of Door Access Control
- Types of Access Control Software
- Types of Access Control Readers
- Access Control Credential Types
- How an Access Control System Works
- Benefits of a Door Access Control System
- Best Door Access Control Systems
- Conclusion
Also, read
As the world becomes more interconnected, the importance of safeguarding your property or business premises has never been more critical. Implementing a robust door access control system can be the key to achieving a secure, efficient, and user-friendly environment, allowing you to manage entry and exit points with ease. In this comprehensive blog post, we’ll explore the world of door access control, breaking down everything from fundamental concepts to cutting-edge solutions available today.
Our goal is to provide you with a thorough understanding of various door access control systems, including their benefits and best practices for implementation. That will hopefully empower you to make an informed decision, when choosing the most suitable door access control system for any building. Get ready for an exciting and informative journey as we unravel the intricacies of door access control solutions and how they can revolutionize your approach to security and facility management. Let’s dive in!
Suggested Posts:
Best Face Recognition Door Locks
What is Door Access Control?
Door access control is a security solution that manages the access and entry of individuals within a building or facility. Access control systems range from simple electronic keypads to complex networked systems that monitor and control access to multiple buildings. These systems simplify facility management by eliminating the need to replace lost keys, track down old keys from terminated employees, or wonder who has access to which areas.
Types of Door Access Control
There are several types of access control systems, each with its own set of features and benefits. Understanding the various types will help you determine the best option for your business.
Discretionary Access Control (DAC)
Discretionary access control is the least restrictive of traditional access control, and the least recommended type of access control for commercial and business security. The DAC model gives business owners, rather than security experts, control over access rights and permissions for all users. Unless the business owner is well-versed in security policies and best practices, DAC is not the best type of access control model.
Mandatory Access Control (MAC)
This type of access control is best-suited for organizations that require high security and confidentiality. Within a MAC paradigm, one person is given authority to establish access guidelines and assign permissions for the entire organization, such as a Chief Security Officer. Mandatory access control gives the administrator sole discretion over access permissions and security clearance.
Role-Based Access Control (RBAC)
A role-based access control paradigm defines permissions by roles assigned to users in the system. Within a business setting, access privileges are often based on employment status and job title, such as allowing management full building access, while contractors or employees from a specific department will only have access to the spaces they need to do their work. RBAC is a user-friendly model and allows administrators to group users and adjust permissions from a central database. RBAC systems usually employ the principles of least privilege and separation of privilege, where users are compartmentalized and given the minimum level of access required to perform their job.
Types of Access Control Software
Access control software is a crucial component of any access control system. Here are three main types of access control management software:
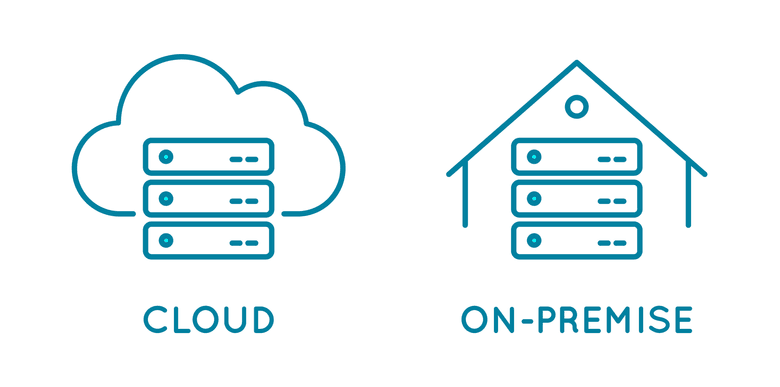
Server-Based Access Control
Traditionally used in large organizations and commercial buildings, on-premise access control systems rely on local servers to host and run software. Server-based access control usually requires the organization to purchase and renew software licenses, and a dedicated IT staff to maintain the servers. If the organization needs access control at multiple locations, they will need servers installed at each site.
Web-Based Access Control
Also known as embedded access control, this type of access control software uses a web browser application to operate access control dashboard and connects to the LAN so that it can be accessed from any device within the network.
Cloud-Based Access Control
Unlike the other two types of access control software, cloud-based software is hosted on a decentralized server, usually managed by a third party, and regularly syncs with local ACUs. Because the system syncs in the cloud, an internet connection is required to support cloud-based access control. In the event of an outage , the ACU will simply sync once the system is back online.
Types of Access Control Readers
Door access control systems use various types of readers and methods to authenticate credentials. Here are some of the most common types:
Keypad Readers
A keypad door reader requires a user to type in a PIN or passcode to unlock the door. Keypad readers offer good security as there is no physical credential that can be passed around or stolen. However, users could still share their PIN with others, compromising building security.
Swipe Card Readers
This type of door card reader works with key cards or badges that have a magnetic strip which contains authentication data. Users swipe their card through the reader in order to unlock the door. One consideration with this type of access control system is the daily wear and tear on the hardware and cards, which means they need to be serviced and replaced more frequently.
RFID Door Readers
Radio frequency identification technology has many uses, including access control. With an RFID access control system, the credentials contain information tags that send signals to nearby readers. Most RFID access control systems use passive RFID, also referred to as proximity or prox card technology. Proximity-based access control systems most often use key cards or key fobs for access.
Biometric Door Readers
Often the most expensive type of door security reader, biometric readers use scanners to identify users by a unique physical feature, such as a fingerprint, iris, or facial recognition. Mobile access control systems with smartphone-based credentials can use the biometrics built into the phone as a form of two-factor authentication.
Smart Lock Door Readers
The most advanced and versatile door security readers on this list, smart readers often combine multiple types of reader technology into one system. Smart readers offer greater flexibility and security with support for mobile credentials, key cards, key fobs, and even touchless unlocking capabilities.
Access Control Credential Types
Different access control systems support various credential types. Here are some of the most common:
- Key cards and badges
- Proximity cards and key fobs
- Biometric credentials (e.g., fingerprint, facial recognition, iris scan)
- PINs or passcodes
- Mobile credentials (e.g., smartphone apps, QR codes)
How an Access Control System Works
An access control system consists of multiple components that work together to manage and revoke access and restrict entry to secured areas within a facility. At its core, an access control system authenticates a user’s credentials and grants or denies access based on predefined rules. Here’s a step-by-step overview of how an access control system works:
Authentication
A user presents their credentials to a door reader, which can be a key card, key fob, PIN, biometric data, or mobile credential.
Verification
The door reader verifies the credential’s authenticity by communicating with the access control panel on site, or cloud-based server.
Authorization
The access control system checks the user’s permissions, considering factors like access levels, time-based restrictions, and location-based rules.
Access Grant or Denial
If the user’s credentials and permissions are valid, the system sends a signal to the door lock to grant access. If the credentials or permissions are invalid, access is denied.
Logging
The access control system logs the event, including details like the user’s identity, date and time, location, and whether access was granted or denied. This information is useful for auditing, reporting, and security analysis.
By implementing a well-designed access control system, organizations can enhance their security posture, protect sensitive assets, and streamline the management of access rights for employees and visitors.
Benefits of a Door Access Control System
A door access control system offers numerous advantages for businesses and organizations of all sizes. By implementing a comprehensive access control solution, you can significantly enhance your security and simplify facility management. Here are some of the key benefits of a door access control system:
Improved Security
Access control systems provide a higher level of security by restricting unauthorized entry and allowing only authorized personnel to access specific areas. This helps protect sensitive information, valuable assets, and critical infrastructure from unauthorized access, theft, or vandalism.
Customizable Access Levels
Door access control systems allow you to assign different access levels for various user groups or individuals. You can grant or restrict access based on job roles, departments, or individual needs, ensuring that employees have access only to the areas they need to perform their duties.
Time and Location-Based Restrictions
Access control systems can enforce time-based and location-based rules, allowing you to limit access during specific hours, days, or under certain conditions. This provides an additional layer of security and ensures that employees can only access areas when it’s appropriate.
Elimination of Physical Keys
By replacing traditional keys with electronic credentials, access control systems reduce the risk of lost or stolen keys and the associated costs of rekeying locks. Electronic credentials can be easily deactivated or reissued, simplifying the management of access rights.
Audit Trails and Reporting
Door access control systems provide detailed logs of entry and exit events, which can be used for security audits, compliance reporting, and investigation of incidents. This information helps you monitor and analyze access patterns, identify potential security risks, and maintain regulatory compliance.
Integration with Other Security Systems
Modern access control systems can integrate with other security solutions, such as video surveillance, intrusion detection, and alarm systems, providing a comprehensive security ecosystem that enhances overall safety and security.
Increased Convenience
Door access control systems provide a seamless and convenient experience for employees and visitors by eliminating the need for physical keys and streamlining the process of entering and exiting secured areas.
Scalability
As your business grows and evolves, access control systems can easily be expanded and adapted to meet changing needs. You can add new doors, users, and access points without significant disruption or expense.
In summary, a door access control system offers numerous benefits that can significantly improve your organization’s security, efficiency, and convenience. By investing in a well-designed door access systems and control solution, you can protect your assets, employees, and facilities while streamlining the management of access rights and permissions.
Best Door Access Control Systems
Swiftlane
Swiftlane is a top solution for door access control systems, offering a range of features that cater to multifamily, commercial and businesses of all sizes. With its cloud-based platform, Swiftlane provides seamless management and scalability for any organization. Some key features of Swiftlane include:
- Touchless access control using facial recognition, mobile credentials, or key cards
- Integration with existing door hardware and access control systems
- Customizable access levels and time-based permissions
- Remote management through a user-friendly web interface
- Easy installation and setup
- Detailed Access Logs: Swiftlane captures comprehensive access logs that include information such as user names, timestamps, and door access points. This data can be used to review and analyze access patterns across your organization, providing insights into potential security risks and unauthorized access attempts.
- Real-Time Monitoring: Swiftlane’s system allows you to monitor access events in real-time, enabling you to respond quickly to any security incidents or suspicious activity. This proactive approach helps maintain a high level of security and prevents potential security breaches.
Swiftlane’s modern approach to door access control provides a secure, flexible, and convenient solution for multifamily buildings or businesses looking to enhance their security, while maintaining ease of use for residents, property owners and managers.
Conclusion
In this comprehensive guide, we have explored the world of door access control systems and their vital role in securing businesses and commercial buildings. Door access control systems offer a modern and efficient way to manage access, ensure security, and maintain control over who enters and exits your facility.
We’ve delved into the various types of access control systems, such as discretionary, mandatory, and role-based access control models, along with the different types of access control software, including server-based, web-based, and cloud-based solutions. We’ve also discussed the range of access control readers and methods, like keypad, swipe card, RFID, biometric, and smart lock door readers, as well as the diverse access control credential types.
The benefits of implementing a door access control system are numerous, from enhanced security and restricted access to sensitive areas, to the convenience of centralized management and streamlined administration. A well-designed door access system can significantly improve overall security, efficiency, and peace of mind for businesses of all sizes.
Among the many door access control solutions available, Swiftlane stands out as a powerful and versatile option, offering unique advantages such as robust audit trail capabilities, real-time monitoring, customizable reporting, historical data access, and seamless integration with other security systems. By carefully considering the various options and selecting the right solution for your needs, you can create a robust and effective access control system that meets the unique requirements of your organization.
Upgrade Your Building Security
Get in touch with a Swiftlane specialist for more information on the best access control and video intercom solution for your building.