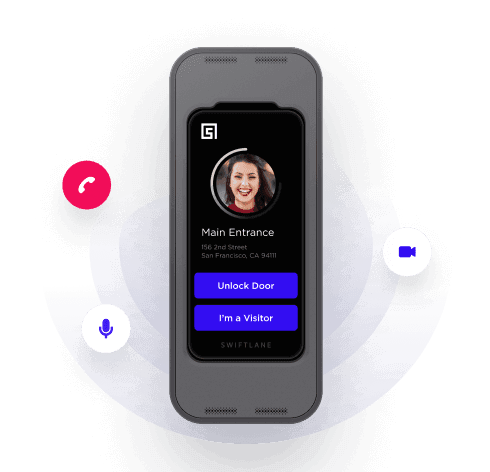
In today’s highly connected and technology-driven world, electronic safety and security have become crucial aspects of modern construction. Protecting and securing our buildings and infrastructure from potential threats is of paramount importance. This blog post delves into the importance of understanding and implementing electronic safety and security in both commercial and residential buildings, as outlined in CSI Division 28: Electronic Safety and Security.

CSI Division 28 encompasses an array of sophisticated technologies and systems that not only protect the occupants and the property itself but also secure sensitive information. Some of the latest trends in electronic safety and security include mobile app access, face unlock, video intercom, and cloud access control systems.
Throughout this blog post, we will discuss in detail the various aspects of electronic safety and security, including the latest innovations and technologies, as well as the challenges and potential risks that we must address. We will also explore how different systems can be integrated to provide a unified, comprehensive approach to security, and the overall role of construction specification experts in ensuring the effective implementation of these systems.
Key Takeaways:
- Electronic safety and security are essential components of modern construction, and CSI Division 28 focuses on these critical aspects.
- Construction specification experts must stay up-to-date with the latest technologies and trends in electronic safety and security.
- Advanced security systems not only protect occupants and property but also secure sensitive information.
- The seamless integration of various security systems can provide a unified, comprehensive approach to security.
Join us in this informative journey as we explore the fascinating world of electronic safety and security, and stay tuned for expert insights and in-depth analysis of the latest trends and technologies. By understanding and implementing these advanced security systems, we can contribute to creating a safer, more secure future for all.
Suggested Posts:
Introduction to CSI MasterFormat and Division 01
Getting to Grips with CSI Division 02 – Existing Conditions in Construction Projects
Mastering Division 09 – Finishes in the CSI MasterFormat System for Improved Project Success
Understanding CSI MasterFormat: Division 14- Conveying Equipment
Master the Art of Utilities Construction with CSI Division 33
Division 48 – A Comprehensive Guide to Electrical Power Generation in Construction
Introduction to CSI Division 28 – Electronic Safety and Security
In today’s fast-paced and interconnected world, the importance of electronic safety and security in modern buildings and infrastructure cannot be overstated. CSI Division 28 includes a broad range of technologies and trends that are shaping the future of security in both commercial and residential buildings. From mobile app access and face unlock systems to video intercoms and cloud access control, these cutting-edge technologies provide enhanced security while also offering improved convenience for users.
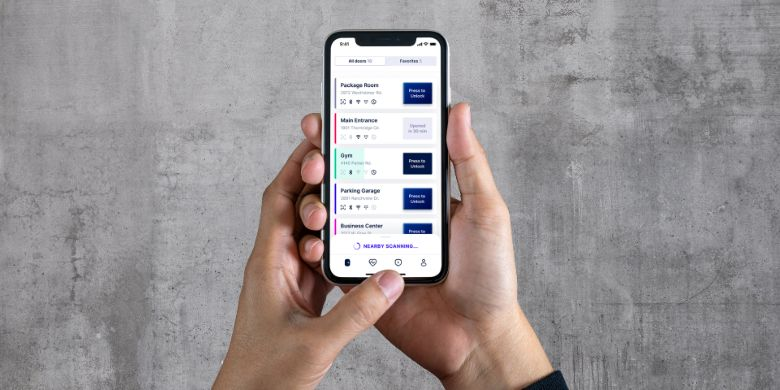
In this blog post, I will explore various aspects of electronic safety and security in detail. From examining the latest advancements in secure entry technology to discussing the benefits of integrated security systems, the goal is to provide readers with a comprehensive understanding of the industry and its ever-evolving landscape. So, let’s dive in and learn more about the world of electronic safety and security!
Mobile App Access and Face Unlock for Secure Entry
Electronic safety and security is constantly evolving, and two of the latest trends in secure entry are mobile app access and face unlock technologies. This section of the blog will provide an in-depth analysis of both methods, discussing their benefits, drawbacks, and technical aspects while comparing them to traditional keycards and physical keys.
Mobile App Access: The Digital Key
Many commercial and residential buildings have already adopted smartphone-based access control systems, allowing authorized users to unlock doors or gates with their phones. This type of access control system relies on digital keys stored on the user’s smartphone, which communicate securely with readers installed on doors or other entry points. These digital keys provide several advantages over traditional keycards, tokens, or physical keys. They are less likely to be lost, stolen, or duplicated, and they can be revoked or adjusted remotely when necessary. Mobile app access also allows for improved user experience, as smartphones are often more convenient and user-friendly than other access control devices.
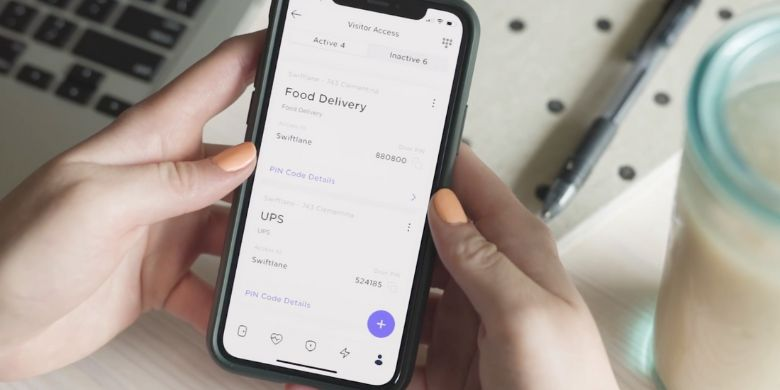
However, drawbacks of mobile app access control do exist. For instance, a user may forget their phone or experience battery issues, leading to difficulties in accessing a building. Additionally, there is the potential for hacking or unauthorized access if effective encryption protocols are not in place.
Face Unlock: Biometric Authentication for Secure Entry
Face unlock technology provides another layer of security by using biometric authentication.- This method measures unique facial features to verify a person’s identity, providing a more secure and seamless authentication process. In comparison to traditional access control systems, face unlock technology can be more convenient and user-friendly. Users do not need to carry around physical keys or access cards, and the authentication process is usually quicker and more intuitive.
However, face unlock technology does come with some potential security risks, such as the possibility of “spoofing” or tricking the system with a photo or video of the authorized user. To counteract these risks, advanced systems often use liveness detection and other anti-spoofing measures.

Balancing Security and Convenience
While mobile app access and face unlock technologies offer increased convenience and user experience, it is essential to ensure that these systems are secure and reliable. This involves using strong encryption protocols, implementing robust cybersecurity measures, and keeping software up-to-date to protect against potential vulnerabilities.
In conclusion, mobile app access and face unlock technologies provide exciting, innovative alternatives to traditional access control systems. By understanding their benefits, drawbacks, and potential security risks, construction specification experts can design and implement electronic safety and security systems that strike the perfect balance between convenience and security. As technology continues to advance, it is crucial to stay informed and adapt to emerging trends in the ever-evolving world of electronic safety and security.

Video Intercom Systems for Enhanced Communication and Security
In today’s world, electronic safety and security are paramount. One essential technology that addresses both communication and security in residential and commercial buildings is the video intercom system.
This section will delve into the various types of video intercom systems, their role in ensuring safety, and the advantages of integrating them with other security measures.
Types of Video Intercom Systems
Video intercom systems can be classified into three main categories based on their connectivity: wired, wireless, and IP-based systems.
- Wired systems – These traditional systems use cables to connect the intercom devices. While they are known for their reliability, they can be more complex and expensive to install, especially in larger buildings.
- Wireless systems – These systems use radio frequencies or Wi-Fi to communicate between devices, offering easier installation and flexibility. However, they may be susceptible to interference from other wireless devices, which can affect their performance.
- IP-based systems – As the most advanced option, IP-based video intercom systems leverage internet connectivity to provide high-quality video and audio, allowing for remote access and control. With the expansion of broadband internet access, these systems have become increasingly popular due to their scalability and flexibility.
Purpose and Functionality of Video Intercom Systems
The primary purpose of video intercom systems is to enhance safety by allowing occupants to visually verify visitors before granting access to a building or specific area. In addition, these systems facilitate communication between different parts of a building, such as between the front desk and individual offices or apartments. Some advanced systems even offer features like remote door release, integration with security cameras, and mobile app access for added convenience.
Integrating Video Intercom Systems with Other Security Measures
To further enhance security, it is crucial to integrate video intercom systems with other security measures such as access control or alarm systems. This integration offers a comprehensive security solution that can help streamline management, improve situational awareness, and enable faster response times during emergencies.

Choosing the Right Video Intercom System and Ensuring Proper Installation
It is essential to select the appropriate video intercom system depending on factors like building size, desired features, and overall security requirements. Proper installation and maintenance are crucial for optimal performance and to avoid potential issues that could compromise safety.
In conclusion, video intercom systems are an indispensable component of electronic safety and security in modern buildings. By understanding the various types of systems, their functionality, and the benefits of integrating them with other security measures, construction specification experts can ensure that the right solution is implemented for enhanced safety and communication in any building or infrastructure project.

Cloud Access Control for Scalable and Flexible Security Solutions
In an era where the need for secure and efficient access control solutions is increasingly important, cloud-based access control systems offer immense advantages over traditional, on-premises systems. In this section, we explore the shift towards cloud-based solutions and discuss their primary benefits, as well as the importance of cybersecurity in safeguarding these systems.
The Shift to Cloud-Based Solutions
The rise of cloud computing has sparked a significant change in the electronic safety and security landscape. The transition from traditional, on-premises access control systems to cloud-based solutions has been driven by the numerous benefits these systems offer. By leveraging the power of the cloud, organizations can benefit from scalable, flexible, and cost-effective security solutions that adapt as their needs evolve.
Benefits of Cloud Access Control
Cloud-based access control systems offer several key benefits over traditional systems:
- Scalability: As a business grows or changes, cloud access control systems can be easily expanded or adjusted to accommodate new locations, employees, or access points, without the need for costly hardware upgrades or rewiring.
- Flexibility: Cloud access control systems can be quickly and easily configured and deployed, allowing organizations to adapt and respond to evolving security requirements.
- Remote Management: Cloud-based solutions enable authorized personnel to manage access control systems from anywhere, at any time, using a web browser or mobile app, streamlining administration and reducing the need for on-site management.
- Cost Savings: With cloud access control, organizations can save on hardware and maintenance costs, and eliminate the need for costly on-premises servers.
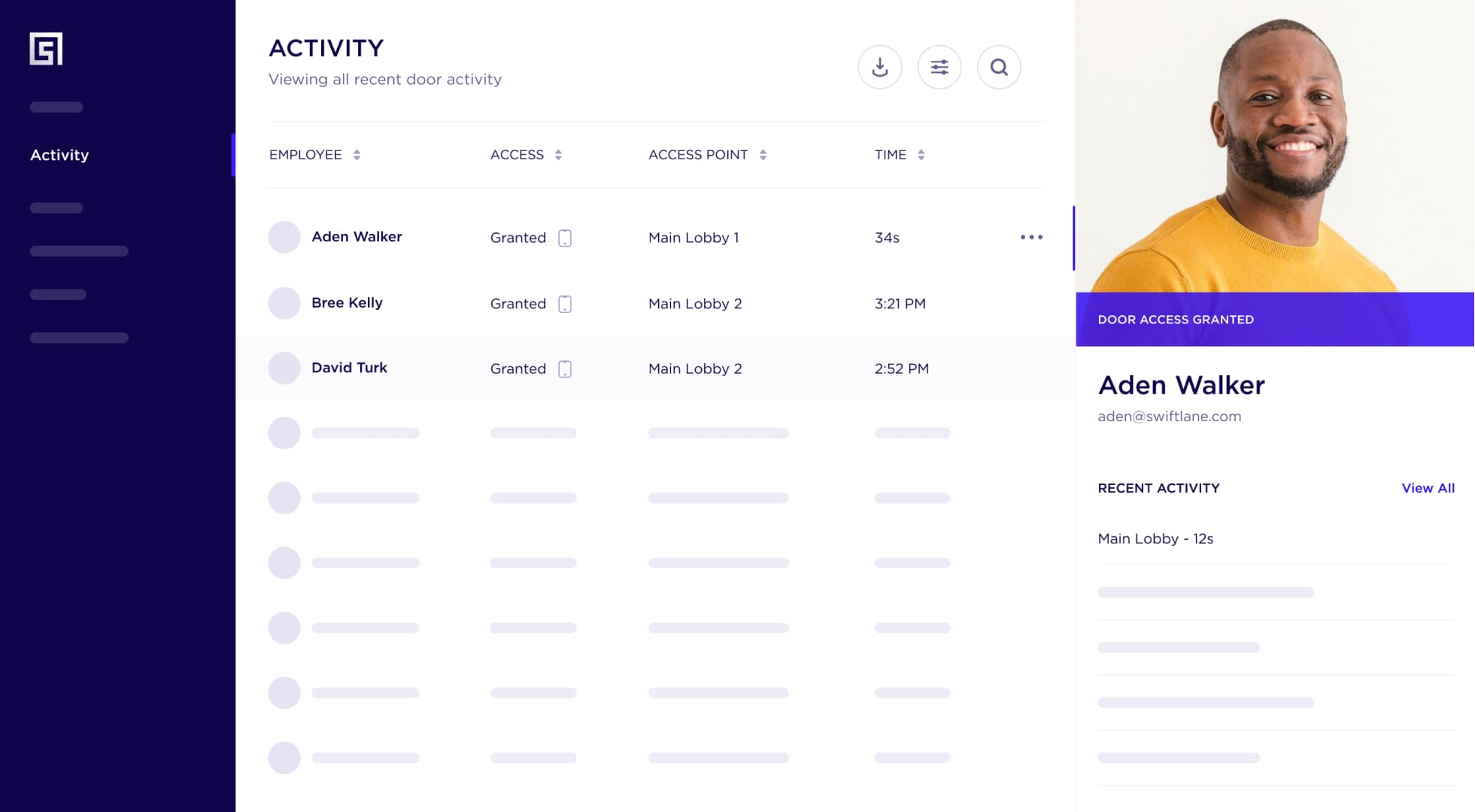
How Cloud Access Control Systems Work
Cloud access control systems use internet-connected devices, such as card readers, biometric scanners, and mobile devices, to authenticate users and grant access to secured areas. These systems rely on a secure connection to a remote server or data center, where user credentials, access permissions, and system configurations are stored.
Various methods of authentication are supported by cloud-based access control systems, including mobile credentials, biometrics, and keycards. This ensures enhanced security and flexibility, allowing organizations to implement the most appropriate methods based on their needs and user preferences.
Cybersecurity in Cloud Access Control
While cloud access control systems offer numerous advantages, they also come with potential security risks. Cybersecurity is a crucial consideration in cloud access control. To safeguard against unauthorized access and data breaches, organizations must follow best practices, such as:
- Implementing strong encryption methods to protect data in transit and at rest.
- Regularly updating software and firmware to address security vulnerabilities.
- Ensuring secure connections between devices and cloud servers using VPNs or other secure communication protocols.
- Implementing multi-factor authentication for system administrators.
Overcoming Challenges in Adopting Cloud Access Control
Despite the numerous benefits of cloud access control, some organizations may face challenges in adopting these solutions, such as concerns about data privacy and regulatory compliance. Construction specification experts play a critical role in guiding organizations in the selection and implementation of secure, compliant cloud access control solutions that meet their unique needs.
In conclusion, cloud-based access control systems offer a more scalable, flexible, and efficient approach to electronic safety and security, providing organizations with the tools they need to protect their people, property, and information. With the rising trend towards connected and integrated security systems, cloud access control will undoubtedly play an increasingly prominent role in the future of electronic safety and security.
Comprehensive Security Solutions: Integrating Multiple Systems
In this section, we’ll explore the concept of integrating multiple security systems to develop a comprehensive, unified approach to electronic safety and security. By combining various systems, we can create a powerful security infrastructure that optimizes situational awareness, simplifies management, and speeds up response times in emergencies.
Benefits of Integrated Security Systems
The primary advantage of integrated security systems lies in their ability to provide a holistic overview of a building or facility’s security. Many commercial and residential buildings have multiple layers of security measures, from access control and video surveillance to alarm systems and building automation. By integrating these systems, security personnel can easily monitor and manage each layer through a centralized interface. Some benefits of integrated security systems include:
- Improved Situational Awareness: Having a single, centralized platform for monitoring all security measures allows for better decision-making and faster response times in the event of an emergency or security breach.
- Streamlined Management: An integrated system simplifies management tasks by providing a unified interface, reducing the need for multiple separate systems and software applications.
- Faster Response Times: With a comprehensive view of all security measures, it is easier to quickly identify and address potential threats or security breaches.
- Easier Upgrades and Expansion: Since integrated systems are designed to work together, adding or upgrading components is typically more straightforward than with disparate systems.
Integration Examples: Access Control, Video Surveillance, and Alarm Systems
To better understand the effectiveness of integrated security systems, let’s look at an example involving the integration of access control, video surveillance, and alarm systems in a commercial building.
By integrating access control with video surveillance, security personnel can verify the identity of individuals entering or exiting the facility in real-time through video footage. This integration allows for both visual and data-driven validation, significantly improving access control measures. Meanwhile, integrating an alarm system with access control and video surveillance enables security personnel to quickly assess the situation when an alarm is triggered.
For example, if an unauthorized entry triggers an alarm, security personnel can immediately verify the intrusion via live video footage and take appropriate action.
Building Automation Integration
Another crucial aspect of integrated security systems is the incorporation of building automation. Building automation systems control and monitor various aspects of a facility, such as heating, ventilation, and air conditioning (HVAC), lighting, and energy consumption.
Integrating these systems with security measures, such as access control and video surveillance, enhances security by allowing facility managers to remotely control and monitor building systems. For example, building automation can help prevent unauthorized access to certain areas by controlling lighting, HVAC systems, or even elevators based on an individual’s access permissions.
Conclusion
Integrated security solutions are a powerful approach to enhancing electronic safety and security in both commercial and residential applications. By combining access control, video surveillance, alarm systems, and building automation, security personnel can effectively manage a facility’s security infrastructure and respond rapidly to security incidents.
Have Questions?
Get in touch with our team to learn more about what Swiftlane can do for you.